CVE-2021–34484: Zero-day vulnerability affects billions of Windows users. No patch available
A recent report details the steps to exploit a zero-day vulnerability in Windows systems whose exploitation would allow threat actors to escalate their privileges to system user under certain conditions. While this is a critical vulnerability, exploitation would require threat actors to know the username and password of two different users, making an attack very difficult in the wild.
In August, released an update to address a vulnerability tracked as CVE-2021–34484, described as an escalation of profile service privileges on Windows systems. Abdelhamid Naceri, a researcher who reported the flaw, analyzed the Microsoft patch and found that this mechanism was insufficient to mitigate the risk of exploitation, and demonstrated an evasion method that he published on GitHub.
According to the expert, Microsoft did not address the error it presented in its report, but only contained the impact of a proof of concept (PoC): “The company only addressed a symptom, or the real cause; the vulnerability of privilege escalation is still present.”
Subsequently, vulnerability analysis specialist Will Dormann tested the flaw and found that the attack could not always be successfully completed.
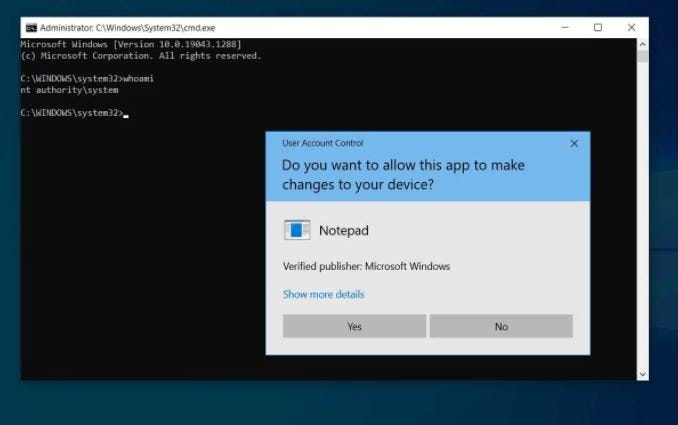
The researcher mentions that the fact that threat actors require knowing the credentials of two different users complicates the exploitation of the flaw in real scenarios. However, the vulnerability exists in all versions of Windows, including Windows 10, Windows 11 and Windows Server 2022, so the risk should not be dismissed by system administrators.
Several members of the cybersecurity community have tried to contact Microsoft to know the official position of the company on this vulnerability, although so far they have not received any response. Many believe that, due to the difficulty of exploitation, the company might not release security patches to address this flaw.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
Originally published at https://www.securitynewspaper.com on October 29, 2021.
